Product overview
Product overview
Database encryption and access control system is a strengthened product to enhance database system and data security, it has sensitive data encryption, permission control, complete transparency, decentralized management, security audit functions, can prevent data theft from internal high-permission users, external attacks and data leakage caused by disk, tape theft etc., to protect the confidentiality and integrity of data. Database encryption and access control system is a strengthened product to enhance database system and data security, it has sensitive data encryption, permission control, complete transparency, decentralized management, security audit functions, can prevent data theft from internal high-permission users, external attacks and data theft caused by disk,
 Funksiɔn Features
Funksiɔn Features
 Dynamic Decryption:Encryption function bɛ data tɔ̈ɔ̈u në database yic ya tɔ̈ɔ̈u në thaa yɛl yic, ka cɔk raan tɔ̈ɔ̈u, ka tɔ̈ɔ̈u në data tɔ̈ɔ̈u, ka tɔ̈ɔ̈u në data tɔ̈ɔ̈u, ka tɔ̈ɔ̈u në data tɔ̈ɔ̈ Kɔn ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye. Sa tɛ̈n yenë raan ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye k
Dynamic Decryption:Encryption function bɛ data tɔ̈ɔ̈u në database yic ya tɔ̈ɔ̈u në thaa yɛl yic, ka cɔk raan tɔ̈ɔ̈u, ka tɔ̈ɔ̈u në data tɔ̈ɔ̈u, ka tɔ̈ɔ̈u në data tɔ̈ɔ̈u, ka tɔ̈ɔ̈u në data tɔ̈ɔ̈ Kɔn ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye kɛ̈n ye. Sa tɛ̈n yenë raan ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye kɔn ye k
 Indeks wɛ̈t:Walisa ka tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ Ka tɛ̈n yenë index looi ku jɔl ya tɛ̈n yenë yen tɔ̈u thïn, ka tɛ̈n yenë yen tɔ̈u thïn, ka tɛ̈n yenë yen tɔ̈u thïn. Ka tɛ̈n yenë wɛ̈t cï gɔ̈t ya tɔ̈ɔ̈u, ka tɛ̈n yenë wɛ̈t cï gɔ̈t ya tɔ̈ɔ̈u, ka tɛ̈n yenë wɛ̈t cï gɔ̈t ya tɔ̈ɔ̈u, Sisitɛm ee teknoloji patente de index de wɛ̈t cï gɔ̈ɔ̈r, ka tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈
Indeks wɛ̈t:Walisa ka tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ tɛmɛ Ka tɛ̈n yenë index looi ku jɔl ya tɛ̈n yenë yen tɔ̈u thïn, ka tɛ̈n yenë yen tɔ̈u thïn, ka tɛ̈n yenë yen tɔ̈u thïn. Ka tɛ̈n yenë wɛ̈t cï gɔ̈t ya tɔ̈ɔ̈u, ka tɛ̈n yenë wɛ̈t cï gɔ̈t ya tɔ̈ɔ̈u, ka tɛ̈n yenë wɛ̈t cï gɔ̈t ya tɔ̈ɔ̈u, Sisitɛm ee teknoloji patente de index de wɛ̈t cï gɔ̈ɔ̈r, ka tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈n yenë tɛ̈
 Teknoloji Key Multi-Level:Field kelen bɛ̈n anɔŋ keys ye tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n t Kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ Key dɔ̈ɔ̈r tɔ̈u në hardware yic, ka tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï Tɛ̈n yenë dual-key technology looi, ka data cï gɔ̈ɔ̈r ka cïï gɔ̈ɔ̈r ka cïï gɔ̈ɔ̈r ka cïï gɔ̈ɔ̈r.
Teknoloji Key Multi-Level:Field kelen bɛ̈n anɔŋ keys ye tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n t Kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ ye kɔlɔ̈ɔ̈ŋ Key dɔ̈ɔ̈r tɔ̈u në hardware yic, ka tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï ya tɛ̈ɛ̈r bï Tɛ̈n yenë dual-key technology looi, ka data cï gɔ̈ɔ̈r ka cïï gɔ̈ɔ̈r ka cïï gɔ̈ɔ̈r ka cïï gɔ̈ɔ̈r.
 Transparent encryption:Data cï gɔ̈ɔ̈r ee tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n Application wala raan dɔ̈ɔ̈ŋ ka cïï bɛ̈n tɛ̈n yenë käke kɔc cï gɔ̈ɔ̈r looi, ka cïï bɛ̈n tɛ̈n yenë käke kɔc cï gɔ̈ɔ̈ Na cï yïn data gël, yïn tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n t
Transparent encryption:Data cï gɔ̈ɔ̈r ee tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n ye tɛ̈n Application wala raan dɔ̈ɔ̈ŋ ka cïï bɛ̈n tɛ̈n yenë käke kɔc cï gɔ̈ɔ̈r looi, ka cïï bɛ̈n tɛ̈n yenë käke kɔc cï gɔ̈ɔ̈ Na cï yïn data gël, yïn tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n tɛ̈n t
 Ajuiɛɛr ye looi:Users can authorize different fields of the same table, defining different access control rights policies, while supporting dual machine heating and key export, preventing system corruption without a key can't decrypt data. Users can authorize different fields of the same table, defining different access control rights policies, while supporting dual machine heating and key export, preventing system corruption without a key can't decrypt data. A dɛmɛ bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ
Ajuiɛɛr ye looi:Users can authorize different fields of the same table, defining different access control rights policies, while supporting dual machine heating and key export, preventing system corruption without a key can't decrypt data. Users can authorize different fields of the same table, defining different access control rights policies, while supporting dual machine heating and key export, preventing system corruption without a key can't decrypt data. A dɛmɛ bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ̈ɛ̈i bɛ
 Database compatibility puɔth:Oracle, MySQL, PostgrelSQL, Daemon, Chengdu Jinshang, Gauss DB, Nanda General Gbase8a, ye database ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc Kä ye kek looi aye luɔ̈ɔ̈i në teknoloji cït encryption plugin, ye kek looi në database yic, ka cïï gam në database yic, ka cïï gam në database yic, ka cïï gam në database yic ku kä ye kek looi në data yic (Hbase, Hive).
Database compatibility puɔth:Oracle, MySQL, PostgrelSQL, Daemon, Chengdu Jinshang, Gauss DB, Nanda General Gbase8a, ye database ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc ye kɔc Kä ye kek looi aye luɔ̈ɔ̈i në teknoloji cït encryption plugin, ye kek looi në database yic, ka cïï gam në database yic, ka cïï gam në database yic, ka cïï gam në database yic ku kä ye kek looi në data yic (Hbase, Hive).
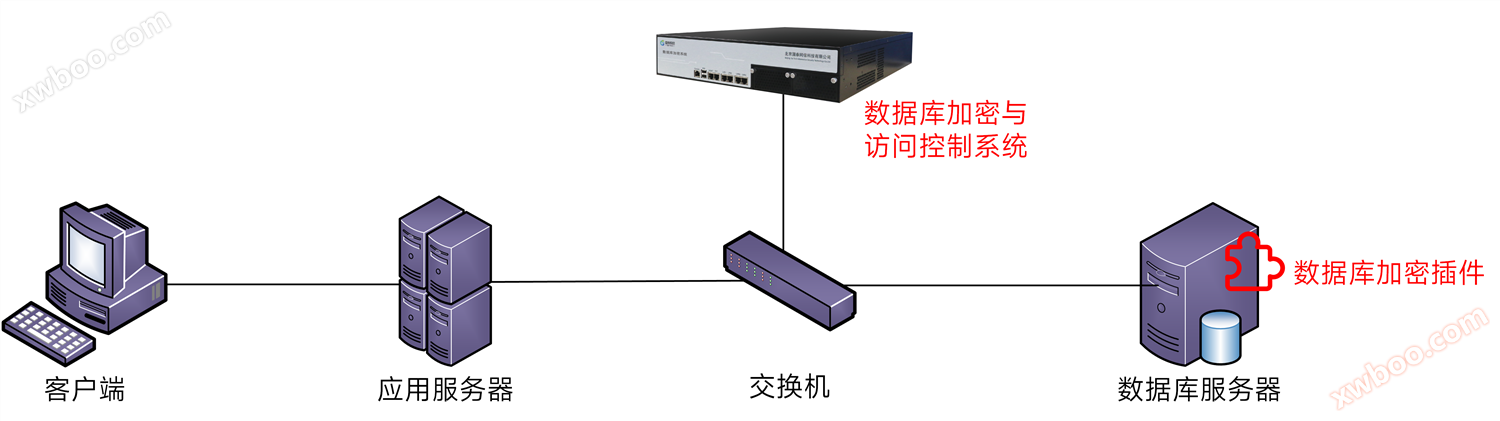
 典型部署
典型部署
Database encryption system deployment is simple, using a bypass deployment method, and can route to reach the database server. Database encryption system deployment is simple, using a bypass deployment method, and can route to reach the database server. Database encryption system deployment is simple, using a bypass deployment method, and can route to reach the database server.